Burpy|一款流量解密插件
【推荐学习】暗月渗透测试培训 十多年渗透经验,体系化培训渗透测试 、高效学习渗透测试,欢迎添加微信好友aptimeok 咨询。
应用场景
Burpy主要用于请求或响应流量加密的安全测试,尤其是涉及金融交易相关的APP,基本都会简单涉及加密或是全流量加密。改插件将BurpSuite和Frida结合了起来,集成使用hook脚本解密流量,极大了提高了渗透测试的效率。
如下图:
项目地址:
https://github.com/mr-m0nst3r/Burpy
使用
界面简单,不做过多介绍. 分别是填写Python路径、解密脚本路径、端口啥的写上就能点击Start Server了,然后到流量界面右击扩展选择加解密。
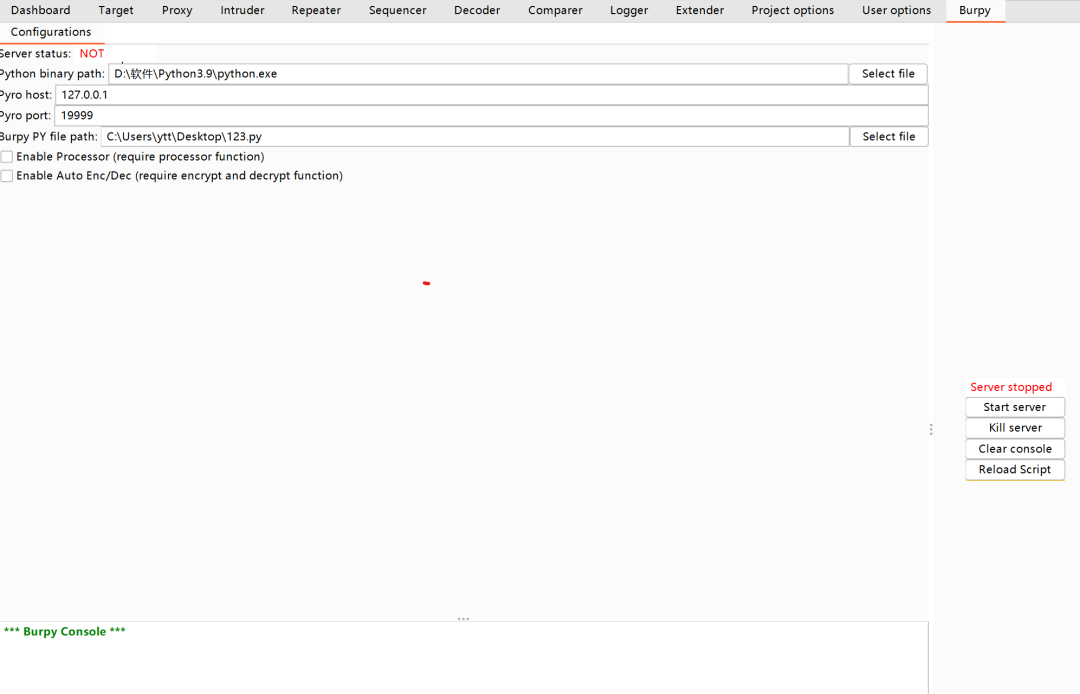
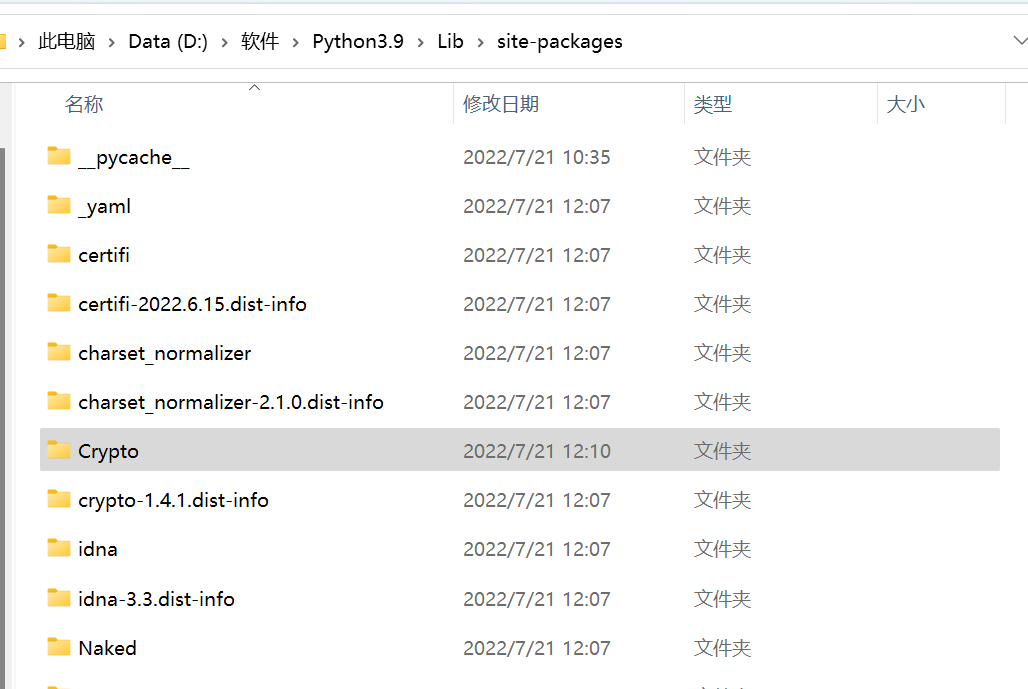
需要注意的是Python3 安装Crypto模块后需要到Python安装目录下的Lib/site-packages/文件夹将crypto文件夹改名为大写的Crypto
初出茅庐
新建一个.py文件,将Burpy脚本路径设置为该文件路径。
class Burpy:
'''
header is dict
body is string
'''
def __init__(self):
'''
here goes some code that will be kept since "start server" clicked, for example, webdriver, which usually takes long time to init
'''
pass
def main(self, header, body):
return header, body
def _test(self, param):
'''
function with `_`, `__`as starting letter will be ignored for context menu
'''
# param = magic(param)
return param
def encrypt(self, header, body):
'''
Auto Enc/Dec feature require this function
'''
header["Cookie"] = "admin=1"
return header, body
def decrypt(self, header, body):
'''
Auto Enc/Dec feature require this function
'''
header["Cookie"] = "admin=2"
# header = magic(header)
# body = magic(body)
return header, body
def processor(self, payload):
'''
Enable Processor feature require this function
payload processor function
'''
return payload+"123"
代码中主要需要注意的是:encrypt/decrypt 负责加解密方法及processor爆破操作payload方法
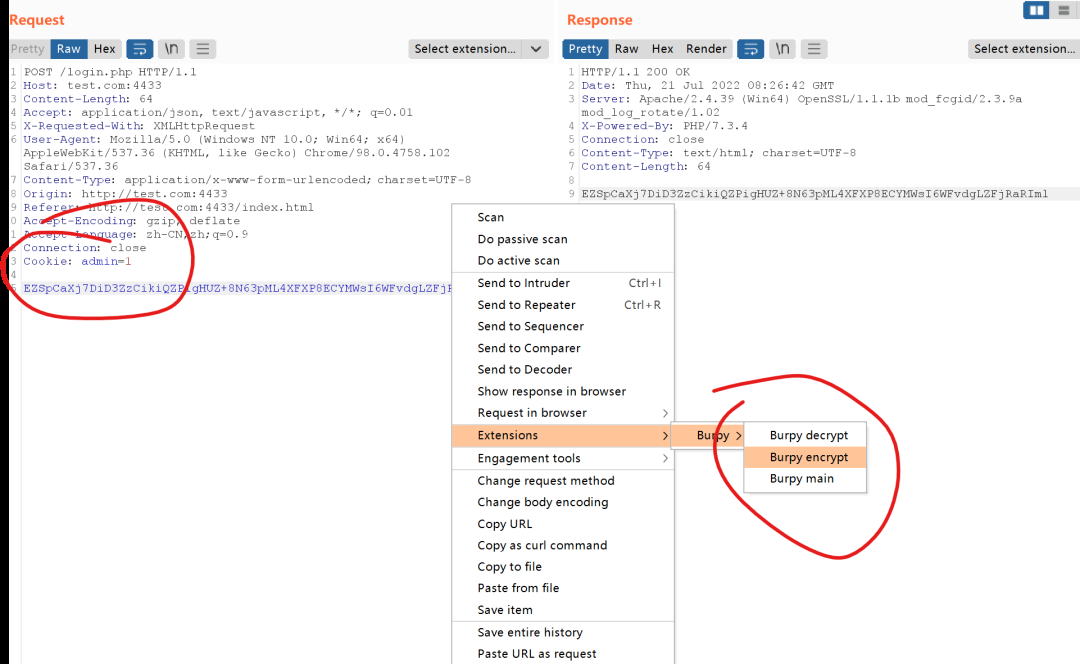
加载脚本运行后,到流量处右击选择Burpy encrypt 请求头就会多出admin=1 字段,该操作再代码encrypt方法中用header["Cookie"] = "admin=1"实现。
小试牛刀
了解了Burpy工作原理后尝试搭建环境进入实战
index.html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>AES加解密测试</title>
<script src="http://cdn.bootcdn.net/ajax/libs/crypto-js/4.0.0/crypto-js.js" type="text/javascript"></script>
<script src="https://cdn.staticfile.org/jquery/1.10.2/jquery.min.js"></script>
<script>
function encrypt(word){
var key = CryptoJS.enc.Utf8.parse("1234567890123456");
var srcs = CryptoJS.enc.Utf8.parse(word);
var encrypted = CryptoJS.AES.encrypt(srcs, key, {mode:CryptoJS.mode.ECB,padding: CryptoJS.pad.Pkcs7});
return encrypted.toString();
}
/**
* 解密
* @param word
* @returns {*}
*/
function decrypt(word){
var key = CryptoJS.enc.Utf8.parse("1234567890123456");
var decrypt = CryptoJS.AES.decrypt(word, key, {mode:CryptoJS.mode.ECB,padding: CryptoJS.pad.Pkcs7});
return CryptoJS.enc.Utf8.stringify(decrypt).toString();
}
function login(data) {
$.ajax({
url:"/login.php",
dataType:"JSON",
method:"POST",
data:encrypt($("#form1").serialize()),
success:function(){
alert($("#form1").serialize());
},
error:function(result) {
var data = encrypt($("#form1").serialize());
document.getElementById("resp").innerHTML = data;
console.log(data)
}
})
}
</script>
</head>
<body>
<form action="####" id="form1" method="post">
name: <input name="userName" type="text">
password:<input name="passWord" type="text">
<input type="submit" onclick="login();return false">
</form>
</br>
AES加密后:<p id="resp"></p>
</body>
</html>
login.php
<?php
$data = file_get_contents("php://input");
echo $data
?>
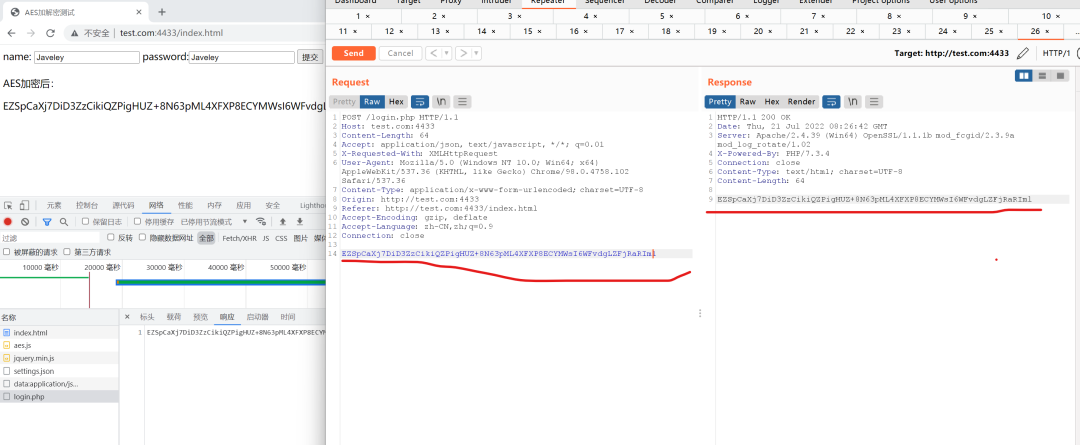
运行结果:
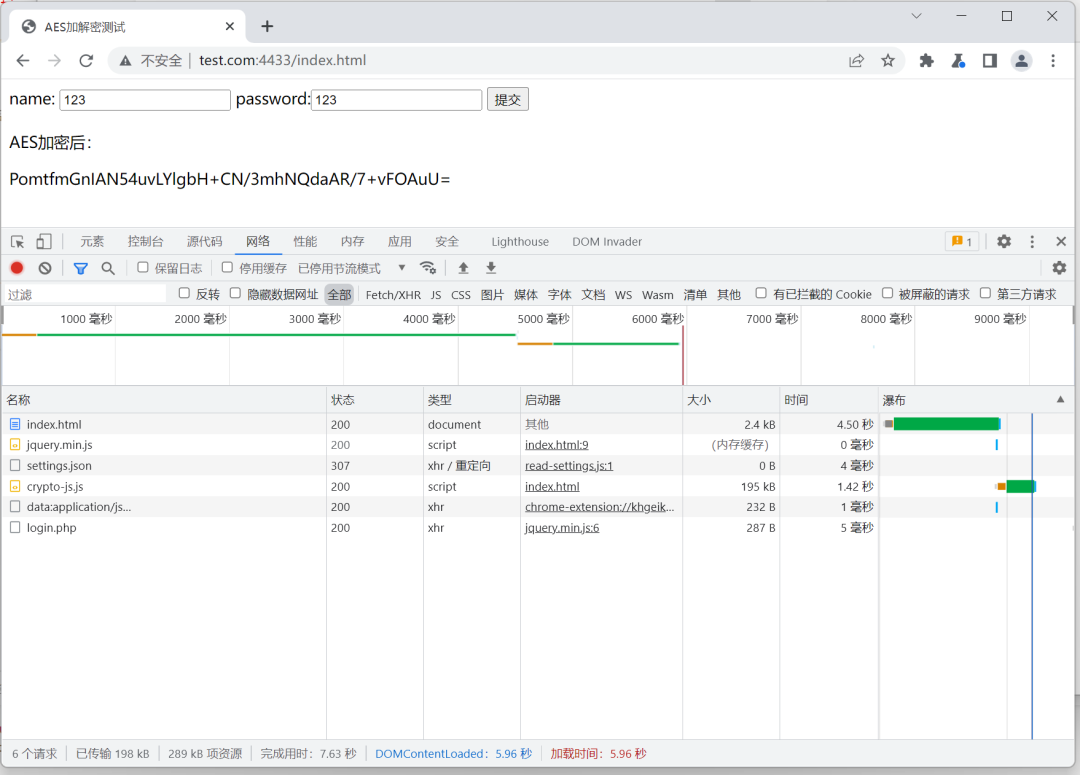
由于是介绍Burpy工具的使用,具体的Js逆向找加密算法就略过了,但是后续应该会专门发些Js笔记系列。
编写流量解密脚本:
class Burpy:
'''
header is dict
body is string
'''
def __init__(self):
'''
here goes some code that will be kept since "start server" clicked, for example, webdriver, which usually takes long time to init
'''
pass
def main(self, header, body):
return header, body
def _test(self, param):
'''
function with `_`, `__`as starting letter will be ignored for context menu
'''
# param = magic(param)
return param
def add_to_16(self,par):
par = par.encode() #先将字符串类型数据转换成字节型数据
while len(par) % 16 != 0: #对字节型数据进行长度判断
par += b'x00' #如果字节型数据长度不是16倍整数就进行 补充
return par
def encrypt(self, header, body):
'''
Auto Enc/Dec feature require this function
'''
return header, body
def decrypt(self, header, body):
'''
Auto Enc/Dec feature require this function
'''
# header = magic(header)
# body = magic(body)
from Crypto.Cipher import AES
import base64
KEY = "1234567890123456"
aes = AES.new(str.encode(KEY), AES.MODE_ECB)
decrypted_text = aes.decrypt(base64.decodebytes(bytes(body, encoding='utf8'))).decode("utf8")
#decrypted_text = decrypted_text[:-ord(decrypted_text[-1])] # 去除多余补位
#body = decrypted_text
print("decrypt:"+decrypted_text)
return header, decrypted_text
def processor(self, payload):
'''
Enable Processor feature require this function
payload processor function
'''
** return payload
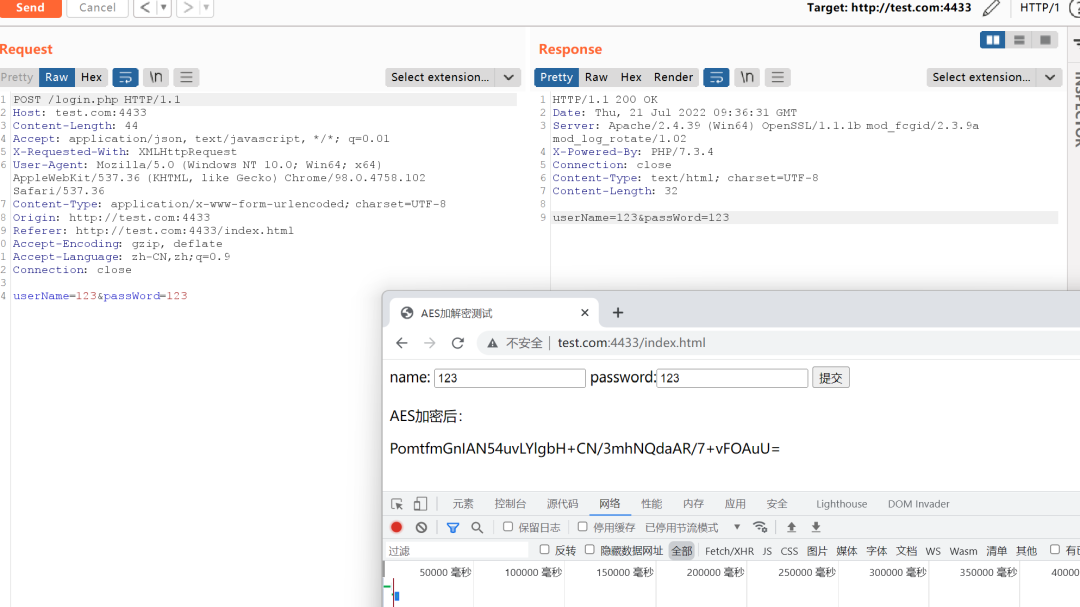
最终效果:想要达到自动加解密的话需要在Burpy界面勾选Enable Auto Enc/Dec(require encrypt and decrypt funciton) 功能
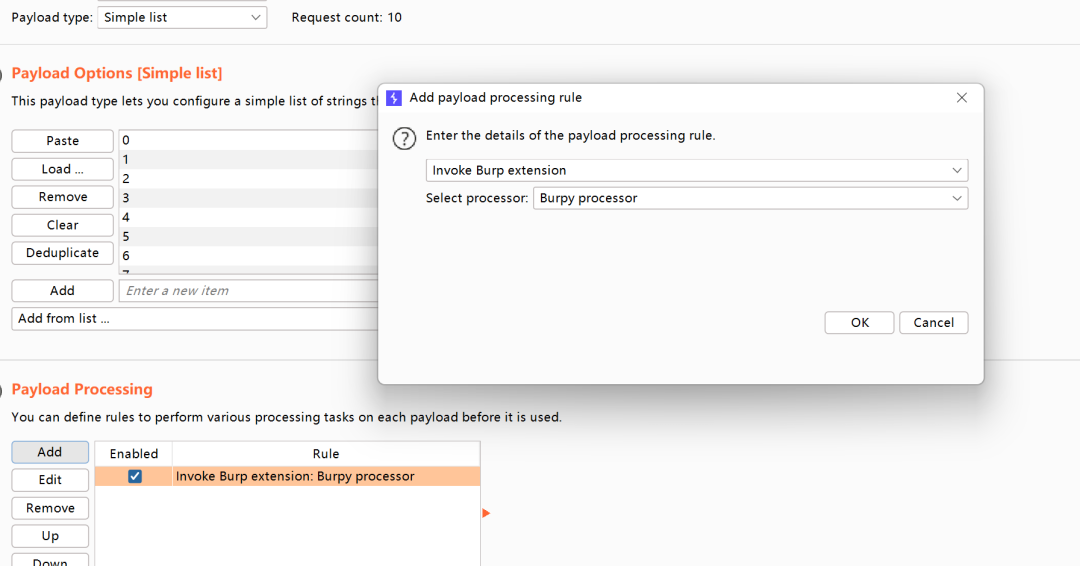
Processor 则是可以处理Intruder模块的Pyloads
原创文章,作者:mOon,如若转载,请注明出处:https://www.moonsec.com/8599.html

